How can we help?
Configuring security settings for a Perfony account
At Perfony, data security and confidentiality are at the heart of our concerns. Since our creation, we have always made it a point of honour to develop a solution that offers not only innovative and high-performance features, but above all a reliable and secure working environment for all our users. Whether in our development processes or in the relationships we maintain with our customers, we show the utmost respect for data confidentiality.
An absolute priority: protecting your data
Data protection is more than just a legal requirement for us; it’s a fundamental commitment. We understand that project management, information exchange and online collaboration are based on mutual trust, and that trust cannot exist without a high level of security. When you choose Perfony, you’re choosing a solution that protects your personal and business data at every stage.
Our infrastructure is designed to ensure maximum security, with strict measures in place to prevent data breaches. This includes robust encryption systems that protect your information, both when it is transmitted and when it is stored on our servers. These measures prevent unauthorised access to your data and guarantee its confidentiality.
Compliance with RGPD regulations
As part of our commitment to data protection, we strictly adhere to the requirements of the General Data Protection Regulation (GDPR). Every Perfony user, whether based in Europe or elsewhere, can be confident that their data is being processed to the highest standards.
For us, compliance with the GDPR implies a high level of transparency in the way we collect, use and store data. We ensure that you can fully exercise your data protection rights, including the right to access, rectify and erase information about you.
Industry-leading standards
At Perfony, we apply the highest, industry-recognised security standards. Our development and technical support teams are trained in the latest advances in cybersecurity, and we regularly update our systems to guard against emerging threats. We carry out frequent security tests to quickly detect and correct any vulnerabilities.
Our systems are also designed to offer high availability and optimum reliability. Whether you’re managing critical projects or confidential information, you can be sure that your data will remain accessible and protected in all circumstances.
Customising security settings
Because every company has specific security needs, we give you the option of adjusting the confidentiality settings to suit your requirements. Whether you want to restrict access to certain functionalities, define stronger password policies or manage user authorisations, Perfony lets you configure your working environment according to your preferences.
We believe that this flexibility is essential in order to guarantee tailor-made security, adapted to the reality of each organisation. So you retain total control over how your data is protected, while benefiting from the robustness and reliability of our platform. The administrator of a Perfony account will be able to access these settings from the settings icon in the top horizontal badeau.
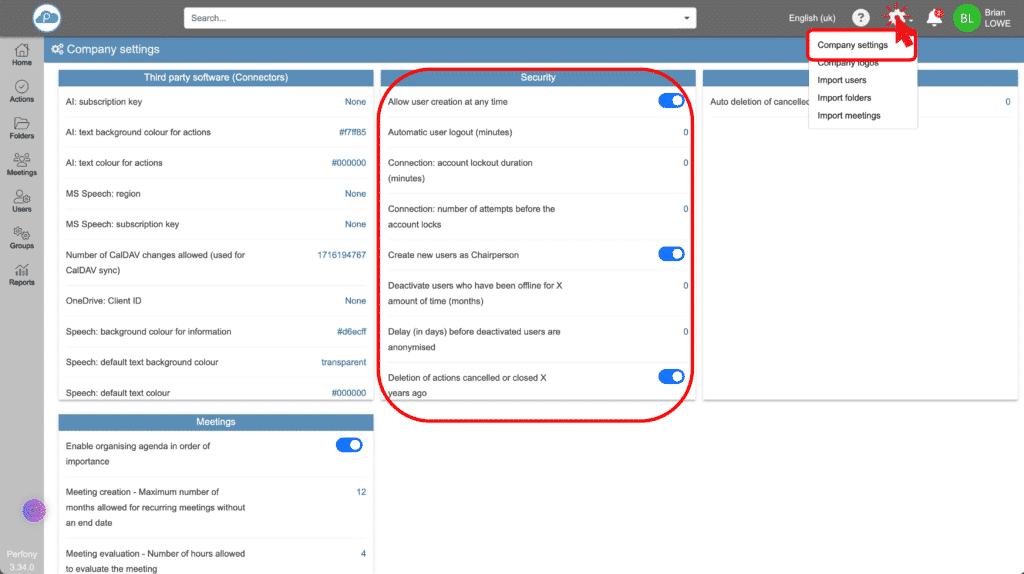
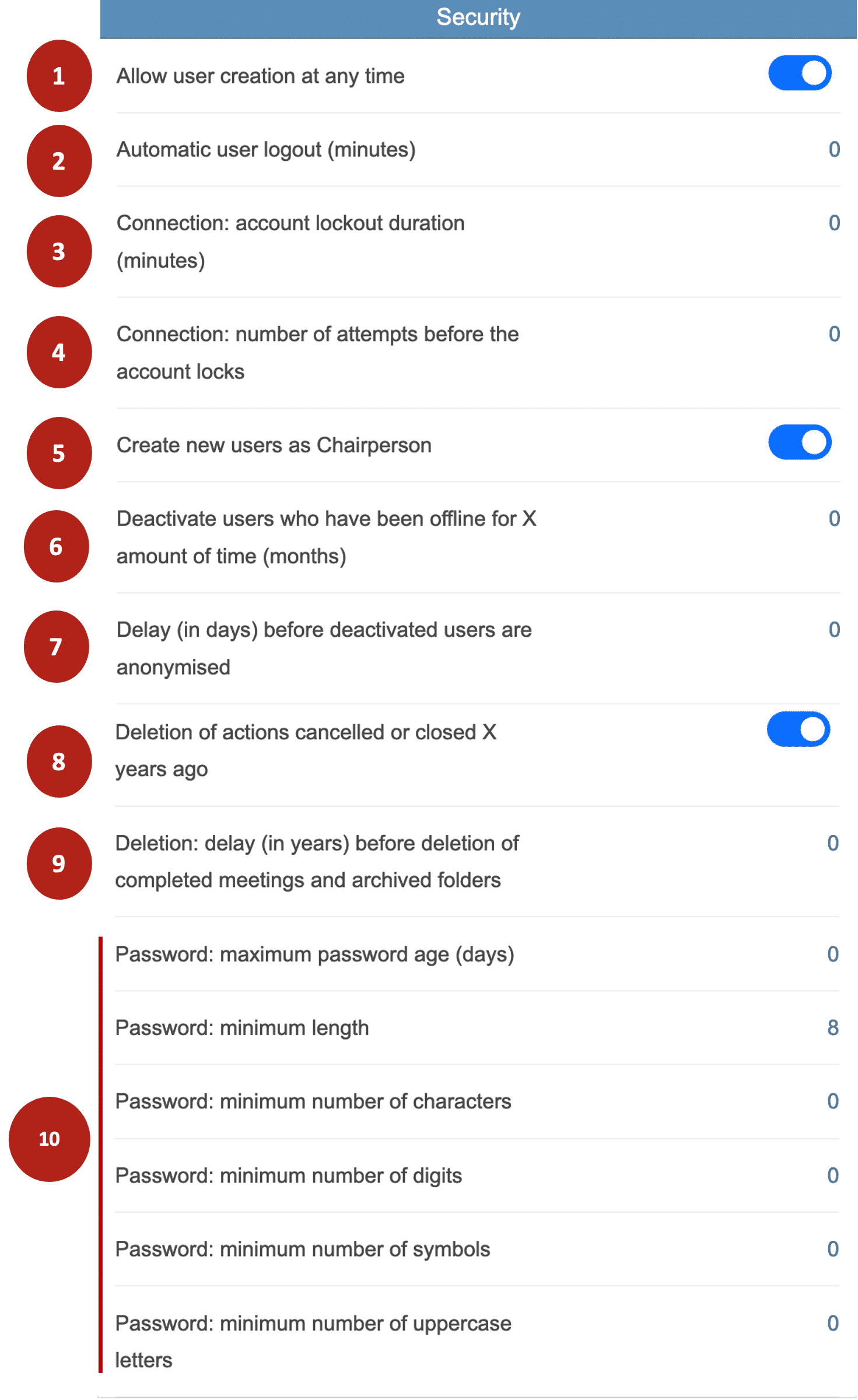
- Allows the Pilot and co-Pilot of a folder or meeting to create users from their folders or meetings without having to be the account administrator and go through the ‘Users’ menu.
- Length of inactivity on Perfony, after which logout is automatic.
- Time during which access to the account is blocked in the event of repeated failed login attempts.
- Number of connection attempts allowed before the account is blocked.
- Determines whether newly created users have ‘Pilot’ rights.
- Duration beyond which a user account without connection will be automatically deactivated. This deactivation is preceded by a warning email 15 days before the deactivation.
- Delay after which deactivated user accounts are anonymised: Surname, First Name, Email are replaced by a random string of characters but they remain in the system and in particular in the actions, folders and meetings in which they previously appeared.
- Time after which cancelled or completed actions are deleted from the system.
- Time after which closed meetings and archived folders are deleted from the system
- Components of the password. Changes to these criteria must be made when the password is renewed.